Snowflake Cloud Datawarehouse Data Encryption and Security
Snowflake is highly secure and has granular permission levels. In this tutorial, you will learn,
- Data Security
- Data Security Features in Snowflake
- User Access control Features in Snowflake
- Data Protection Features in Snowflake
- Data Encryption
- End-to-End Encryption
- Client-Side Encryption
Data Security Features in Snowflake
- Automatic data encryption by Snowflake using Snowflake-managed keys.
- All communication and data transfer between clients and the server protected through TLS
- You can Choose the geographical location where your data is stored, based on your cloud region
- Support for PHI data (in compliance with HIPAA regulations) — requires Business Critical Edition.
- Deployment inside a cloud platform VPC (AWS) or VNet (Azure).
- Isolation of data (for loading and unloading) using:
- Amazon S3 policy controls
- Azure SAS tokens
- Google Cloud Storage access permissions
User Access control Features in Snowflake
- User authentication through standard user/password credentials.
- Enhanced User authentication:
- Multi-factor authentication (MFA)
- Federated authentication and single sign-on (SSO)
- OAuth
- Object-level access control
Data Protection Features in Snowflake
- Snowflake Time Travel (1 day standard for all accounts; additional days, up to 90, allowed with Snowflake Enterprise)
- Snowflake Fail-safe (7 days standard for all accounts) for disaster recovery of historical data
Data Encryption
Snowflake encrypts all customer data by default, using the latest security standards, at no additional cost. Snowflake provides best-in-class key management, which is entirely transparent to customers
End-to-End Encryption
End-to-end encryption (E2EE) means the data is encrypted as it leaves the user till it gets loaded and vice versa. In Snowflake, this means that only a customer and the runtime components can read the data. No third parties, including Snowflake’s cloud computing platform or any ISP, can see data in the clear
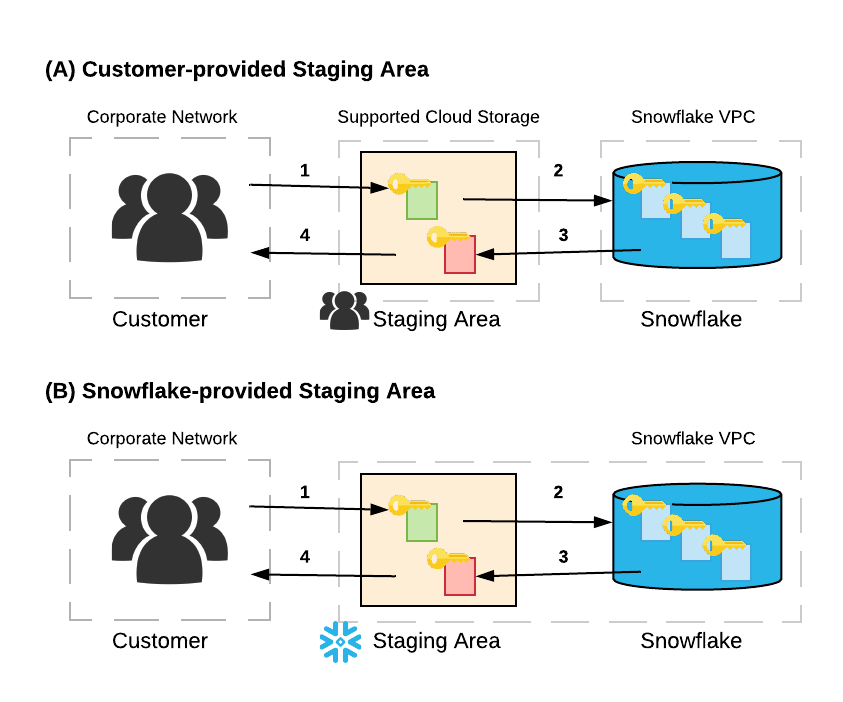
In the above example:
A user uploads one or more data files to a stage. If the stage is a customer-managed container in a cloud storage service (option A), the user may optionally encrypt the data files using client-side encryption. regardless, Snowflake immediately encrypts the data when it is loaded into a table. If the stage is an internal (i.e. Snowflake: option B), data files are automatically encrypted by the client on the local machine prior to being transmitted to the internal stage
The user loads the data from the stage into a table. The data is transformed into Snowflake’s proprietary file format and stored in a cloud storage container (“data at rest”). In Snowflake, all data at rest is always encrypted
Query results can be unloaded into a stage. Results are optionally encrypted using client-side encryption when unloaded into a customer-managed stage, and are automatically encrypted when unloaded to a Snowflake-provided stage
When the user downloads data files from the stage and decrypts the data on the client side
E2EE minimizes the attack surface. In the event of a security breach of the cloud platform, the data is protected because it is always encrypted, regardless of whether the breach exposes access credentials indirectly or data files directly, whether by an internal or external attacker
Client-Side Encryption
Client-side encryption provides a secure system for managing data in cloud storage. Client-side encryption means that a user encrypts stored data before loading it into Snowflake. The cloud storage service only stores the encrypted version of the data and never includes data in the clear
The Snowflake customer creates a secret master key, which remains with the customer.
The client (provided by the cloud storage service) generates a random encryption key and encrypts the file before uploading it into cloud storage. The random encryption key, in turn, is encrypted with the customer’s master key.
Both the encrypted file and the encrypted random key are uploaded to the cloud storage service. The encrypted random key is stored with the file’s metadata.
If you are using client side encryption, Snowflake will need the keys to read the files. The following SQL snippet creates an example Amazon S3 stage object in Snowflake that supports client-side encryption
-- create encrypted stage
create stage encrypted_customer_stage
url='s3://customer-bucket/data/'
credentials=(aws _key_id='ABCDEFGH' aws_secret_key='12345678')
encryption=(master_key='eSxX0jzYfIamtnBKOEOxq80Au6NbSgPH5r4BDDwOaO8=');