Encryption Key Management in Snowflake (KMS)
Security is quintessential when it comes moving all your data to the cloud. At Snowflake, all data in your cloud data warehouse is encrypted by default, using latest security standards and best practices, at no additional cost
There are three important concepts with Key Management Systems (KMS)
Hierarchical Key Model
A hierarchical key model is the highlight of Snowflake’s encryption key management. A key hierarchy has several layers of keys where each layer of keys (the parent keys) encrypts the layer below (the child keys). When a key encrypts another key, security experts refer to it as “wrapping”. In other words, a parent key in a key hierarchy wraps all of its child keys
Snowflake’s hierarchical key model consists of four levels of keys:
- The root key
- Account master keys
- Table master keys
- File keys
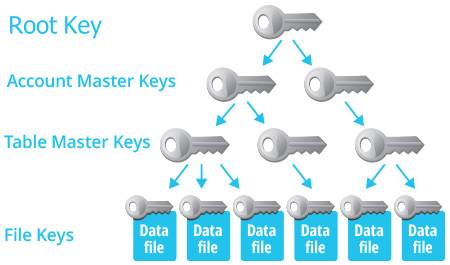
As the name implies, Each account master key corresponds to one customer account in Snowflake. Each table master key corresponds to one database table in a database. That means that every account and every table is encrypted with a separate key. Similarly, every single data file is encrypted with a separate key.
Hierarchical key models are super unique, as each layer of keys reduces the scope of their applicability. For example, table master keys reduce the scope of their applicability to single tables; file keys further reduce the scope of applicability to single files. Thus, a hierarchical key model is essential to constrain the amount of data each key protects, and the duration of time during which it is usable
Encryption Key Rotation
Account and table master keys are automatically rotated by Snowflake when they are more than 30 days old. Active keys are retired, and new keys are created. When Snowflake determines the retired key is no longer needed, the key is automatically destroyed. When active, a key is used to encrypt data and is available for usage by the originator. When retired, the key is used solely to decrypt data and is only available for usage by the recipient. When wrapping child keys in the key hierarchy, or when inserting data into a table, only the current, active key is used to encrypt data. When a key is destroyed, it is not used for either encryption or decryption. Regular key rotation limits the lifecycle for the keys to a limited period of time
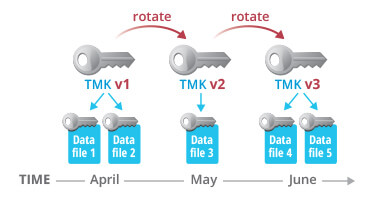
Version 1 of the TMK is active in April. Data inserted into this table in April is protected with TMK v1.
In May, this TMK is rotated: TMK v1 is retired and a new, completely random key, TMK v2, is created. TMK v1 is now used only to decrypt data from April. New data inserted into the table is encrypted using TMK v2.
In June, the TMK is rotated again: TMK v2 is retired and a new TMK, v3, is created. TMK v1 is used to decrypt data from April, TMK v2 is used to decrypt data from May, and TMK v3 is used to encrypt and decrypt new data inserted into the table in June.
Encryption Keys - Rekeying
Rekeying is the process of re-encrypting data with new keys. After a specific time interval, data that has been encrypted with an old key gets re-encrypted with a new key
Key rotation = “new data gets fresh keys”, Rekeying = “old data gets fresh keys”
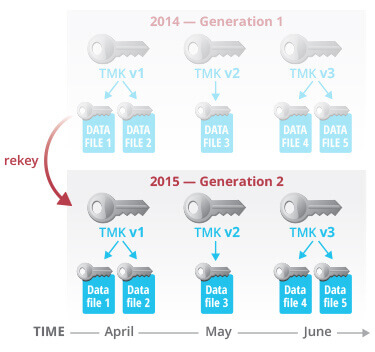
The TMK in this figure is rotated every month, as was explained in the previous section. In addition, the TMK in Figure 3 is rekeyed after one year. That is, in April 2015, TMK v1 is rekeyed. A new generation 2 of TMK v1 is created, a fully new random key. The data files protected by TMK v1, generation 1 are decrypted and encrypted with TMK v1, generation 2. Because all data files are now protected with a new TMK, the old TMK v1, generation 1 can be destroyed; it is not used anymore. In this example, the life cycle of a key is limited to a total duration of one year. The benefit of rekeying is that it constraints the total duration during which a key is used for recipient usage
Data that is being rekeyed is always available to the customer. No downtime of the service is necessary to rekey data and no performance impact is observed on the customer workload. You will be charged with additional storage for Fail-safe protection of 7 days of data files storage that were rekeyed
Additional Security measures:
Hardware Security Module : Snowflake relies on your cloud-vendors hardware security module (HSM) services as a tamper-proof, highly secure way to generate, store, and use the root keys of the key hierarchy
Tri-Secret Secure and Customer-Managed Keys: With Tri-Secret Secure enabled for your account, Snowflake combines your key with a Snowflake-maintained key to create a composite master key. This composite master key is then used to encrypt all data in your account. If either key in the composite master key is revoked, your data cannot be decrypted, providing a level of security and control above Snowflake’s standard encryption. This dual-key encryption model, together with Snowflake’s built-in user authentication, enables the three levels of data protection offered by Tri-Secret Secure